How does Nginx use ModSecurity?
Nginx uses ModSecurity to protect against Cross-Site Scripting (XSS) attacks, Denial of Service (DoS) attacks, SQL injection attacks, command injection attacks, buffer overflow attacks and clickjacking. This protection is achieved by inspecting HTTP requests and responses using rules specified in a flexible configuration file (which uses similar syntax to Apache’s mod_rewrite). If you are using Nginx as a reverse proxy for another application or service, you may want to forward requests to another application or service for further processing; however, if you no longer want to process request and response data, using Nginx as a reverse proxy with ModSecurity keeps your web server safe from some of the OWASP Top 10 vulnerabilities.A Web Application Firewall (WAF) is software designed to protect one or more applications deployed behind it. An added benefit of using ModSecurity as an HTTP firewall is that, unlike many WAF solutions that only offer basic filtering capabilities - such as detecting directory traversal attempts - other inspection capabilities can also be implemented without significant impact on system performance thanks to the nginx architecture that was originally developed for high-traffic websites with exceptional performance requirements.
Why should I use ModSecurity?
In short, WAFs (Web Application Firewalls) are becoming increasingly popular for protecting servers from DDoS attacks and other web threats. A WAF acts as a firewall for your site, filtering out traffic that could endanger your site or impact page load times. It can also monitor activity on your site to report any anomalies that might suggest a potential attack or scam. The basic principle of a WAF is to check URLs against a set of rules you have defined to identify malicious traffic. It is similar to anti-virus software in many ways, but tailored specifically to websites. If an item passes through a WAF filter, it should be safe to distribute on your site. However, if an item fails, it will be blocked before it reaches your website. Because of these properties, sites that use a WAF report fewer malicious requests - because they don’t even reach their server - and faster responses due to reduced bottlenecks in site performance caused by malicious requests. This means increased protection without slowing down access to your content or causing slower load times.
Why should I use both Nginx and ModSecurity?
The reason you should combine Nginx with ModSecurity is that Nginx does not have any real security capabilities on its own. It would still be vulnerable to SQL injections, cross-site scripting (XSS) and many other types of attacks. In order to protect your application, you will need a WAF (Web Application Firewall). Using Nginx in front of a WAF will add an extra layer of protection between your web application and malicious users. What sets ModSecurity apart from most other WAFs on the market is that it is an open source project, which means that anyone can contribute patches, report bugs and submit feature requests, all without paying a license fee. As new contributors are added to the core ModSecurity team, new features will always be deployed quickly, so that website owners have access to all kinds of protection against emerging threats as soon as possible. Since its release in 2002, ModSecurity has become one of the most popular standalone PHP applications available today! All developers who use or implement ModSecurity in their projects have free access to high quality software that only gets better with time. Today, millions of people and businesses rely on ModSecurity for their daily needs. By combining Nginx and ModSecurity into a single Nginx + ModSec stack, websites will benefit from increased performance while enjoying increased levels of protection that would not be available if they were using these technologies separately.
Why should I use both Nginx and ModSecurity?
The reason you should combine Nginx with ModSecurity is that Nginx does not have any real security capabilities on its own. It would still be vulnerable to SQL injections, cross-site scripting (XSS) and many other types of attacks. In order to protect your application, you will need a WAF (Web Application Firewall). Using Nginx in front of a WAF will add an extra layer of protection between your web application and malicious users. What sets ModSecurity apart from most other WAFs on the market is that it is an open source project, which means that anyone can contribute patches, report bugs and submit feature requests, all without paying a license fee. As new contributors are added to the core ModSecurity team, new features will always be deployed quickly, so that website owners have access to all kinds of protection against emerging threats as soon as possible. Since its release in 2002, ModSecurity has become one of the most popular standalone PHP applications available today! All developers who use or implement ModSecurity in their projects have free access to high quality software that only gets better with time. Today, millions of people and businesses rely on ModSecurity for their daily needs. By combining Nginx and ModSecurity into a single Nginx + ModSec stack, websites will benefit from increased performance while enjoying increased levels of protection that would not be available if they were using these technologies separately.
How to configure ModSecurity on Hidora
It’s really basic! We provide ModSecurity as an addon for your Nginx nodes. All you have to do is install this addon and ModSecurity will be activated and configured for your application! You don’t need to know much about security, we are here to help you! With Hidora, all our customers have access to our team of expert security engineers who analyze, fix and monitor all threats that could impact your applications in real time.
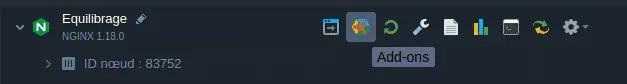
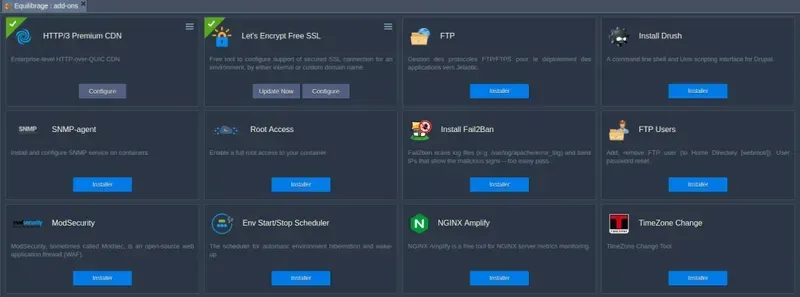
It’s done! Modsecurity is now installed and configured for your Nginx node 🙂…