Network security emerges as a critical concern as you orchestrate your containerized applications with Kubernetes. The dynamic nature of container networking demands real-time detection of abnormal behavior, ensuring that only authorized services access your data. Yet, challenges persist—traffic encryption, thorough container-to-container traffic analysis, and seamless integration with existing network security tools are essential to safeguard your infrastructure.
Enter NeuVector, an open-source, zero-trust security solution designed for Kubernetes environments that provides robust container networking security throughout its lifecycle.
This article will explore NeuVector’s capabilities and essential best practices for implementing an effective Kubernetes security strategy with it.
NeuVector’s Security Approach: More Than Just Network Security
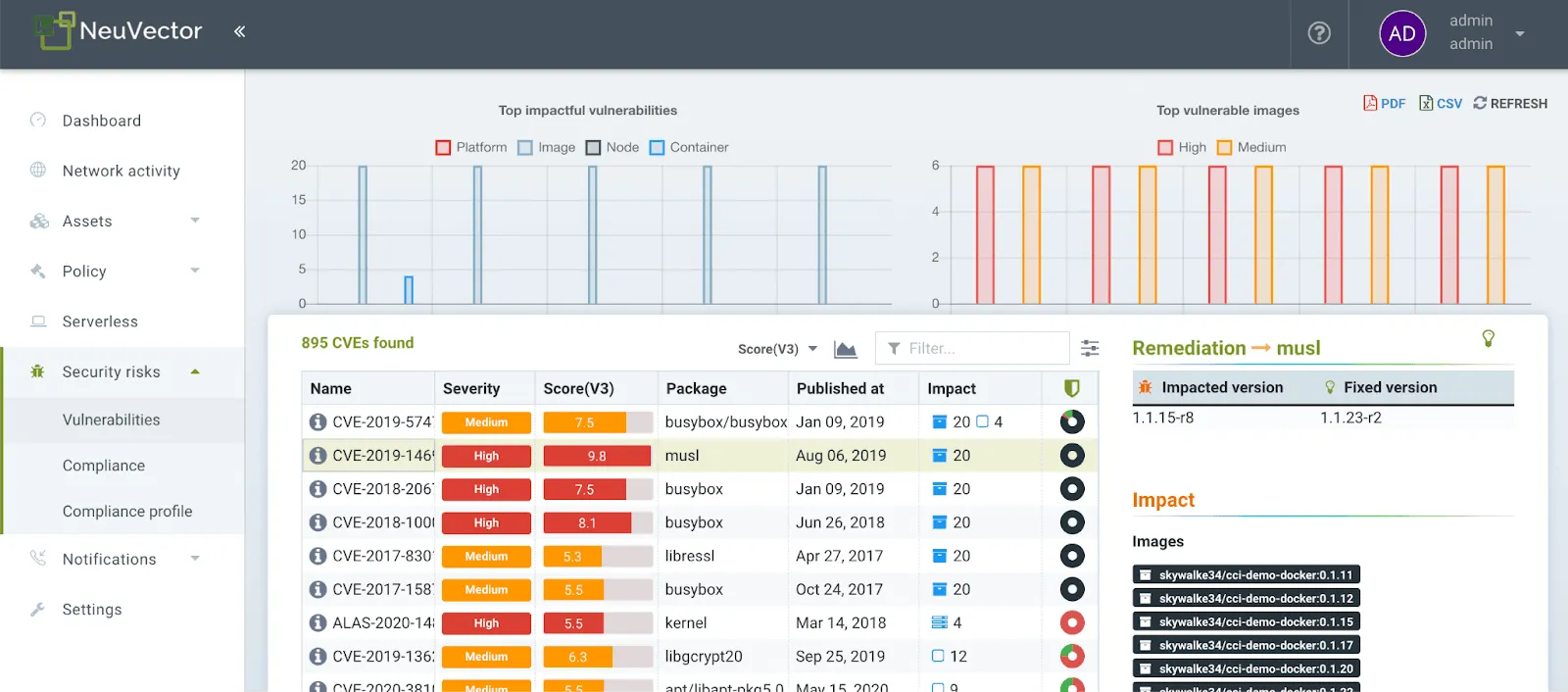
Before delving into NeuVector’s network security features, it’s essential to understand that its capabilities extend well beyond mere network defenses. NeuVector is an all-encompassing vulnerability management system for your CI/CD pipeline, providing continuous scans for container vulnerabilities from the initial build phase through testing and deployment.
Critical features of NeuVector include admission control scans during the build, test, and deployment stages, which are essential to maintaining a fortified security stance. NeuVector also offers automated compliance assessments and reporting that align with the Center for Internet Security (CIS) benchmarks, simplifying compliance management and ensuring adherence to regulatory standards. Additionally, NeuVector conducts real-time scans of containers, hosts, and Kubernetes to prevent attacks, safeguarding your environment throughout the container lifecycle.
Now that we’ve established NeuVector’s role as a container vulnerability management solution let’s explore how it enhances the security of your Kubernetes network.
Real-time Network Visibility, Monitoring, and Protection with NeuVector
NeuVector provides network-specific security features designed to protect your Kubernetes applications. Let’s examine them closely.
Deep Packet Inspection for Security and Debugging
At the core of NeuVector’s network security strategy is its robust deep packet inspection (DPI) capability. Unlike traditional firewalls that merely inspect packet headers, NeuVector examines the data within the packet, enabling it to uncover and block sophisticated network attacks that might otherwise go undetected. Moreover, DPI’s granularity facilitates debugging and threat investigation, providing a powerful forensic tool to analyze and respond to security incidents.
Layer 7 Container Firewall: Advanced Runtime Security
NeuVector’s exclusive Layer 7 container firewall is one of its most advanced runtime security measures. By focusing on the application layer, NeuVector controls traffic based on container behavior, ensuring that only legitimate requests are processed. This unique approach provides precise control and protection, safeguarding your applications from both known and novel threats that can bypass traditional security mechanisms.
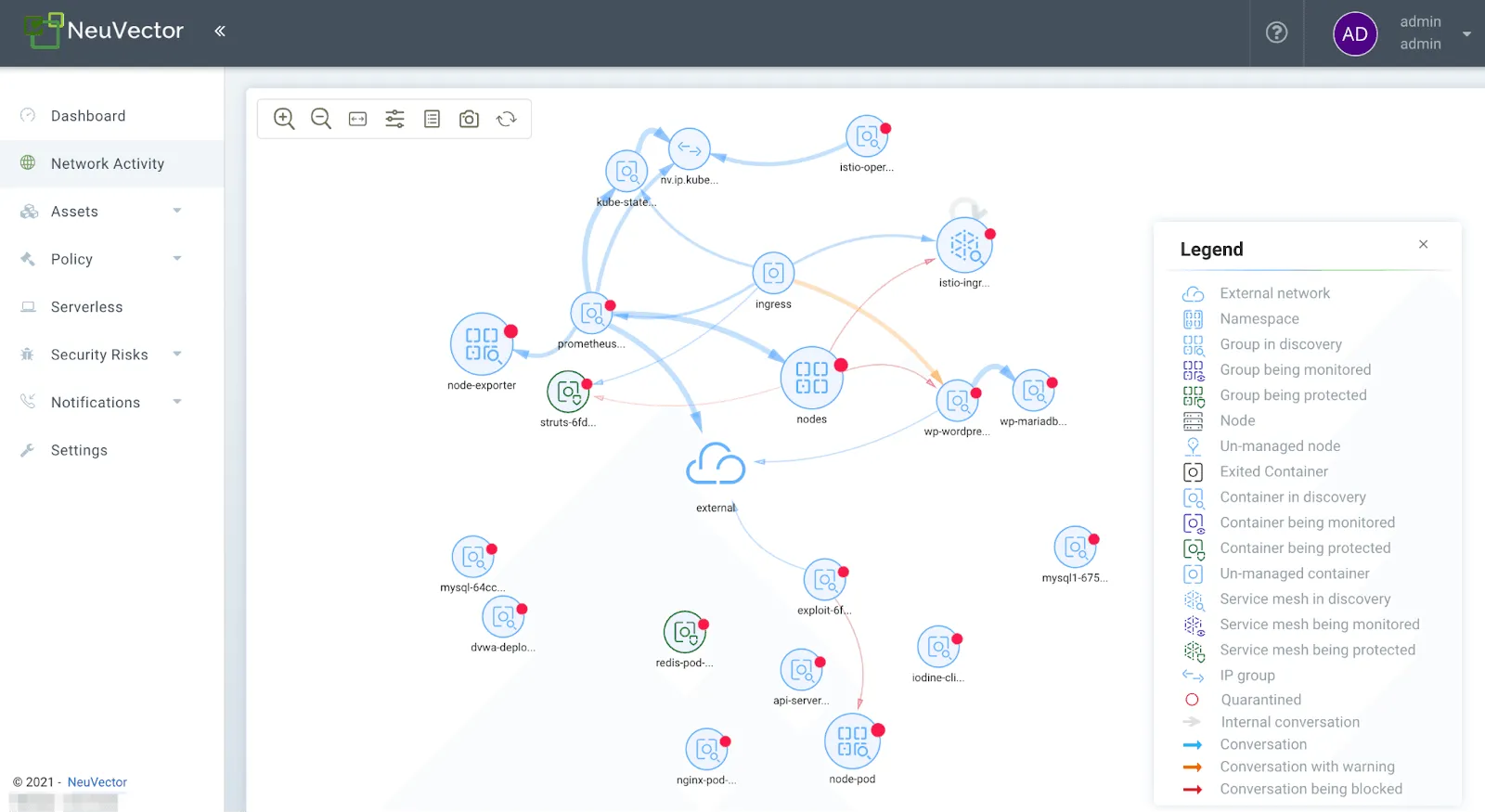
Monitoring ‘East-West’ and ‘North-South’ Traffic
NeuVector’s network visibility extends to both ‘East-West’ traffic, which refers to the communication within your Kubernetes cluster, and ‘North-South’ traffic, which encompasses the data exchanged between your cluster and external services.
By monitoring these traffic flows in real-time, NeuVector detects anomalous patterns and potential threats, allowing for immediate response. This comprehensive monitoring ensures that every vector of network communication is under constant surveillance, minimizing the risk of breaches and data leaks.
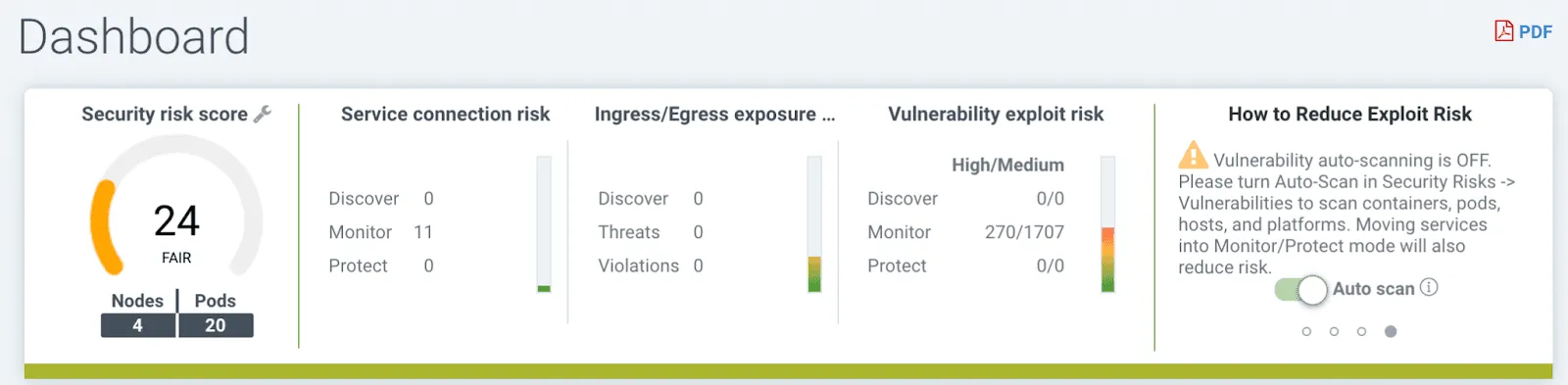
Best of all, the monitoring results are presented on the dashboard using a security risk score for each area of interest, like the Ingress/Egress Risk Score. By clicking on any of these indicators, a wizard can guide your team through the recommended steps to reduce the threat level.
Container Segmentation: Isolating Sensitive Information
One of NeuVector’s standout features is its container segmentation capability, which enforces that only authorized connections between containers are allowed using specific protocols.
This segmentation is critical for compliance with data protection regulations and helps prevent unauthorized access to sensitive data. By segmenting containers, NeuVector enforces strict access controls, limiting the potential damage from compromised containers and enhancing your security posture.
Automated Threat Response and Network Policies
In addition to its monitoring capabilities, NeuVector automates threat response, swiftly reacting to detected threats by implementing predefined network policies. These policies can be tailored to suit your security requirements, ensuring that even the most subtle of anomalies trigger an appropriate response. NeuVector’s policy-driven approach to security streamlines the protection process, reducing the need for manual intervention and allowing for a more proactive defense strategy.
Integration with Cloud and Hybrid Environments
NeuVector isn’t limited to a single environment. It seamlessly integrates with multi-cloud and hybrid environments, providing consistent network security across various platforms. This flexibility ensures that no matter where your containers are deployed, NeuVector’s network protection travels with them, offering a unified security solution that adapts to your infrastructure.
Continuous Compliance and Audit Readiness
Beyond immediate threat detection and response, NeuVector also supports ongoing compliance efforts. Its continuous compliance features scan for vulnerabilities and ensure that your network adheres to regulatory standards. With audit-ready reporting, NeuVector simplifies the compliance management process, providing clear, actionable insights to maintain a secure and compliant network environment.
Best Practices for Maintaining Robust Security into Kubernetes
As discussed, NeuVector goes beyond network security. You can use it to integrate robust security measures and maintain a strong defense within your Kubernetes cluster. Here’s how.
- Automate Security in CI/CD Pipelines: Integrate NeuVector into your CI/CD workflows for automated scans of container images. This catches vulnerabilities early, preventing them from reaching production.
- Update Security Policies Regularly: Keep your NeuVector security policies current to counter new threats effectively and ensure compliance with the latest standards.
- Leverage Admission Controls Integration: When using this integration, NeuVector controllers assess each attempt to create a Kubernetes resource based on user-defined Admission Control rules. Depending on these rules, the controller decides whether to allow or deny the creation of the cluster resource.
- Real-Time Scanning and Protection: Deploy NeuVector’s continuous scanning of network traffic and container activities within your Kubernetes cluster to detect and block threats instantly.
- Monitor and Audit Continuously: Continuously monitor your environment and audit container activities to maintain high-security awareness and response, ensuring that any potential threats are identified and addressed promptly to safeguard your infrastructure.
By implementing these practices, you can ensure robust, automated security that reduces the reliance on manual intervention.
Conclusion: Strengthening Kubernetes Security with NeuVector
To summarize, NeuVector provides extensive, real-time network visibility, monitoring, and protection tailored for Kubernetes environments. Leveraging advanced DPI technology and a unique Layer 7 container firewall, it offers detailed traffic monitoring and container segmentation to mitigate network threats effectively. Its policy-driven automation and compatibility with cloud and hybrid platforms enhance security measures, making it a critical component for maintaining a secure, resilient, and compliant container network infrastructure.







